Introduction
In previous analyses, we have carefully tracked the evolution of phishing trends and the growing threats they have posed over the past several years. These observations have shown a marked increase in the sophistication and frequency of phishing attacks, highlighting a concerning trajectory as cybercriminals continuously refine their strategies to exploit vulnerabilities in digital communication networks. As we move forward, it is crucial to understand these trends in detail to anticipate and mitigate potential security risks associated with phishing.
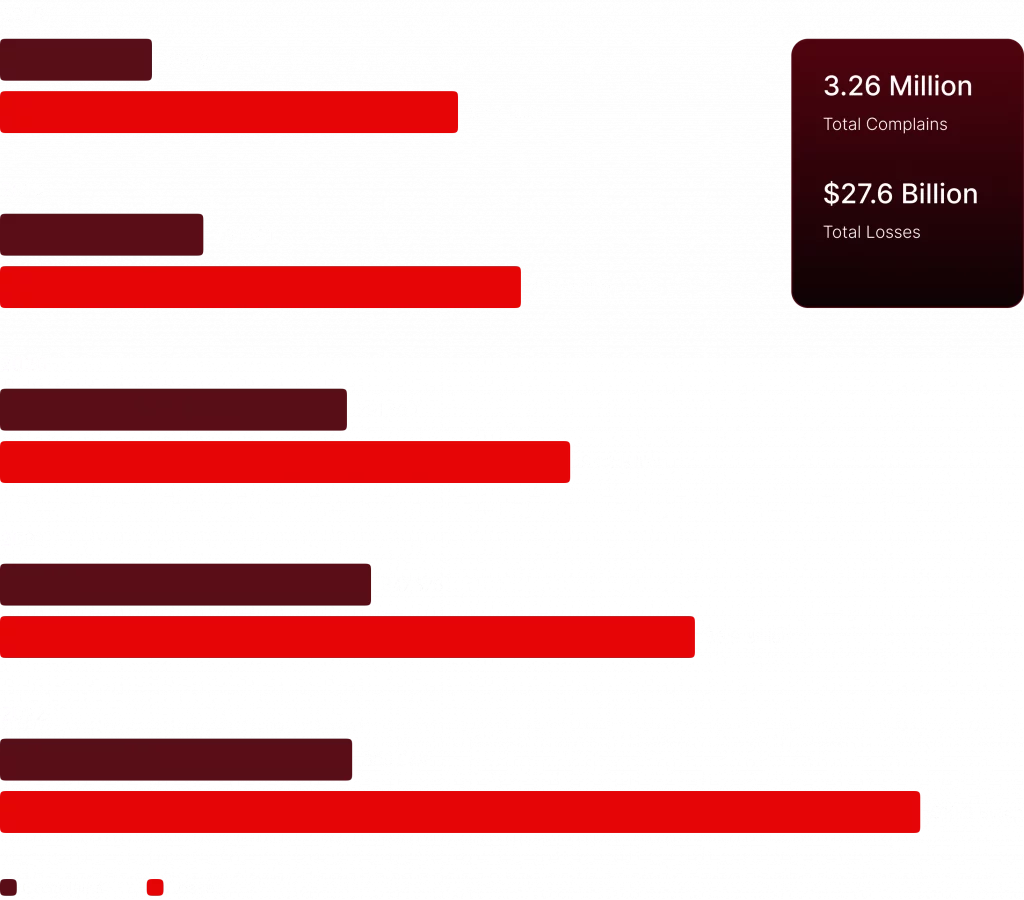
The Internet Crime Complaint Center (IC3) receives an average of 651,800 complaints annually and has accumulated over 7.3 million reports since its establishment in 2000. In 2022, victims incurred the highest financial losses in the program’s history, totaling $10.2 billion.
Phishing remains one of the most pervasive and insidious threats in the digital age, constantly evolving to exploit new platforms and technologies. Traditionally associated with deceptive emails that steal personal information, phishing tactics have seamlessly transitioned into social media, exploiting its vast, interconnected networks. With billions of users exchanging personal details, business data, and more, social media platforms present a fertile ground for cybercriminals. They leverage these platforms’ inherent trust and casual nature to manipulate users into divulging sensitive information or unknowingly spreading malware. As these attacks become more sophisticated, understanding the nuances of social media phishing is essential for protecting personal and corporate assets. This article delves into the mechanics of phishing scams on social media. It explores how they operate, why they are particularly effective, and what can be done to mitigate the associated risks.
Understanding Social Media Phishing
Phishing attacks on social media are particularly insidious because they leverage these networks’ personal connections and the informal, trusting nature. Unlike traditional phishing, which often involves unsolicited emails from unknown entities, social media phishing often appears to come from familiar contacts or reputable organizations.
Common tactics include:
- Fake Profiles: Creating accounts that mimic real users or organizations to send malicious links.
- Quizzes and Games: Enticing users to participate in seemingly harmless activities that harvest personal data.
- Compromised Accounts: Using hacked accounts to spread scams among networks of trust.
- Message Spoofing: Sending direct messages that appear to come from friends urging clicks on malicious links.
The Impact of Phishing Scams
The consequences of these phishing attacks are far-reaching:
- Personal Data Theft: Loss of sensitive personal information that could lead to identity theft.
- Financial Fraud: Direct loss from stolen credit card details or deceptive transactions.
- Corporate Espionage: Breaches that lead to the loss of strategic business information.
- Reputation Damage: Harm to personal or brand reputation due to disseminating harmful content.
Cybersecurity Measures for Social Media
To combat the threat of social media phishing, both individuals and organizations must adopt comprehensive cybersecurity strategies:
- Education and Awareness:
- Conduct regular training sessions to recognize phishing attempts.
- Stay updated on the latest phishing techniques and preventive measures.
- Use Advanced Security Tools:
- Employ robust antivirus software that offers real-time protection against malware.
- Implement two-factor authentication (2FA) to add an extra layer of security.
- Privacy Settings and Permissions:
- Adjust privacy settings to limit the amount of shareable personal information.
- Regularly review and manage app permissions to ensure minimal access to personal data.
- Regular Monitoring and Reporting:
- Monitor social media accounts for any unusual activity.
- Report and remove suspicious content and profiles to help platforms improve security measures.
- Backup and Recovery Plans:
- Ensure that data is regularly backed up and that a recovery plan is in place in case of data loss.
Conclusion
As social media continues to grow, so does the sophistication of phishing scams targeting these platforms. Awareness and proactive measures are crucial in mitigating the risks posed by these cyber threats. By understanding the tactics used by cybercriminals, regularly updating security practices, and fostering a culture of cybersecurity awareness, ind
