In today’s hyper-connected, data-driven world, the digital landscape has become as perilous as it is essential. Cyberattacks are no longer isolated or rare events; they are a persistent, evolving threat that touches every industry and organization, regardless of size or sector. From crippling ransomware attacks and devastating data breaches to insider threats, operational errors, and natural disasters, the potential for disruption looms large. For modern organizations, the conversation has shifted from if they will face a disruption to when.
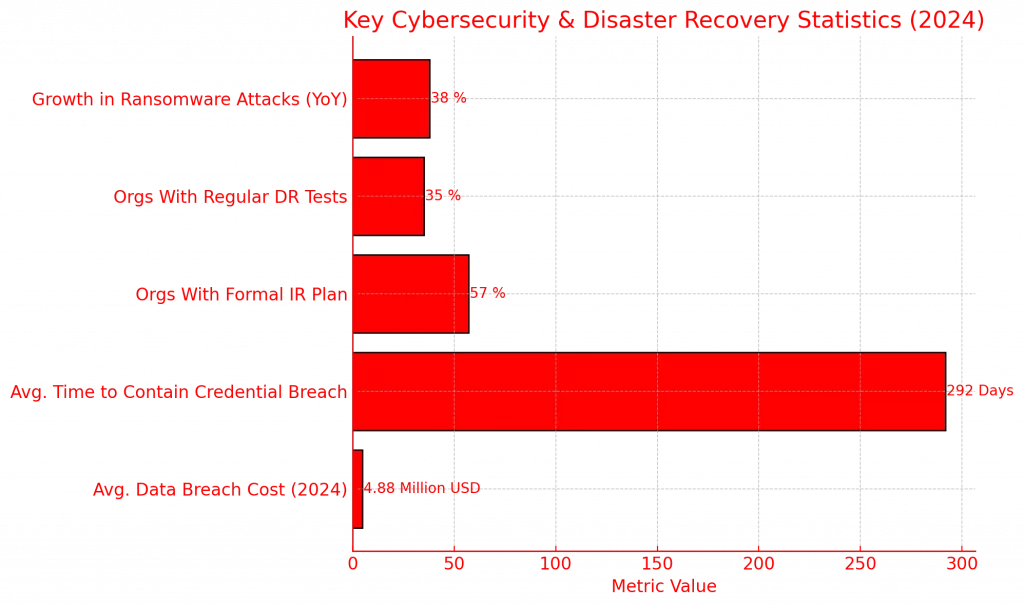
The financial, reputational, and operational costs of these incidents can be staggering. Yet, the organizations that consistently emerge stronger from crises aren’t necessarily the ones with the largest cybersecurity budgets — they are the ones with the most meticulously crafted and rigorously tested Incident Response (IR) and Disaster Recovery (DR) strategies. Together, these two pillars form the cornerstone of cyber resilience: the capacity to withstand, respond to, and recover from disruptive events while maintaining business continuity.
This article dives deep into the strategic principles, critical elements, and proven best practices required to build an effective IR and DR framework capable of safeguarding your organization in the face of uncertainty.
Understanding the Distinction: Why You Need Both IR and DR
One of the most common mistakes organizations make is conflating Incident Response and Disaster Recovery. While they are interconnected, they address different challenges at different stages of a cyber crisis.
Incident Response (IR)
IR is the frontline defense. It focuses on the immediate detection, analysis, containment, and eradication of security incidents such as ransomware, malware infections, data breaches, denial-of-service attacks, and insider misuse. The goal is swift action to mitigate damage and prevent further compromise.
Disaster Recovery (DR)
DR takes over once the dust begins to settle. It focuses on restoring IT operations, data integrity, and critical services following a catastrophic event. Whether the root cause was cyber-related, environmental, or accidental, DR minimizes downtime and ensures the rapid resumption of normal business activities.
The Symbiotic Relationship
Think of IR as the team that stops the bleeding, while DR is the surgeon that repairs the wound and restores function. Seamless communication and coordination between these teams is essential for a smooth transition from incident containment to operational recovery.
1. Assembling Your Incident Response Team (IRT)
People are the heart of any response capability. A well-prepared Incident Response Team must be cross-functional, available 24/7, and empowered to act decisively without bureaucratic delays.
Key Roles Include:
- Incident Response Manager: Orchestrates the response efforts and serves as the liaison with executive leadership.
- Security Analysts & Threat Hunters: Detect, investigate, and neutralize malicious activities using forensic tools and threat intelligence.
- IT Operations Staff: Execute containment measures such as isolating compromised systems and restoring services from backups.
- Legal & Compliance Advisors: Ensure actions comply with regulations like GDPR, HIPAA, or CCPA, and manage legal exposure.
- PR & Communications Specialists: Coordinate internal and external messaging to mitigate reputational damage and maintain stakeholder trust.
Outsourcing Capabilities
Smaller organizations may lack the internal resources for a full-scale IRT. Partnering with Managed Security Service Providers (MSSPs) or retaining an external incident response firm ensures access to expert support when it’s needed most.
2. Designing a Comprehensive Incident Response Plan (IRP)
Without a clear, actionable plan, even the most talented team will struggle under pressure. Your IRP should define roles, outline procedures, and establish escalation paths for every type of potential incident.
The NIST Incident Response Lifecycle (SP 800-61)
- Preparation:
- Train employees in security awareness.
- Develop playbooks for common attack scenarios.
- Deploy logging, monitoring, and alerting systems.
- Train employees in security awareness.
- Identification:
- Detect suspicious activity and confirm incidents.
- Categorize based on severity and impact.
- Detect suspicious activity and confirm incidents.
- Containment:
- Short-term: Quarantine affected systems.
- Long-term: Patch vulnerabilities and block malicious access.
- Short-term: Quarantine affected systems.
- Eradication:
- Remove malware, close attack vectors, and clean up compromised systems.
- Remove malware, close attack vectors, and clean up compromised systems.
- Recovery:
- Restore systems from trusted backups.
- Monitor for signs of persistence or secondary attacks.
- Restore systems from trusted backups.
- Lessons Learned:
- Conduct post-incident reviews to improve defenses.
- Update policies, controls, and training.
- Conduct post-incident reviews to improve defenses.
Common Pitfalls to Avoid:
- Inadequate documentation
- Communication failures
- Delayed decision-making
- Neglecting legal and regulatory obligations
3. Building an Effective Disaster Recovery Plan (DRP)
If IR handles the crisis, DR ensures your business survives it. A strong DR plan prepares your organization to bounce back from the brink.
Key Components:
- Business Impact Analysis (BIA): Identify mission-critical processes and their dependencies.
- Recovery Time Objective (RTO): The maximum acceptable downtime.
- Recovery Point Objective (RPO): The maximum acceptable data loss interval.
- Data Backup & Replication: Automate frequent backups and ensure offsite or cloud storage.
- Redundant Systems: Implement failover solutions for vital infrastructure.
Disaster Recovery Sites:
- Cold Sites: Empty spaces prepared for setup (longest recovery time).
- Warm Sites: Pre-equipped spaces that require final configuration.
- Hot Sites: Fully operational replicas of your environment ready for instant failover.
The Rise of DRaaS
Cloud-based Disaster Recovery as a Service (DRaaS) offers organizations scalability, speed, and cost efficiency, making enterprise-grade DR accessible even for mid-sized businesses.
4. The Critical Role of Drills and Simulations
A plan is only as good as its execution under pressure. Regular training and simulated exercises transform theory into instinct.
Types of Exercises:
- Tabletop Drills: Walk-through scenarios to test communication and coordination.
- Simulated Attacks: Red teams emulate real-world attacks to uncover vulnerabilities.
- Full Interruption Tests: Controlled shutdowns to validate failover and recovery protocols.
Why Practice Matters:
- Identify gaps and undocumented dependencies.
- Train staff to operate under real-world stress.
- Validate response and recovery time objectives.
- Demonstrate compliance to auditors and regulators.
5. Best Practices for Sustainable IR and DR Programs
- Secure Executive Buy-In: Leadership must champion and fund these programs.
- Integrate IR and DR Efforts: Avoid siloed teams and conflicting priorities.
- Maintain Thorough Documentation: Keep all procedures, contacts, and escalation plans updated and accessible.
- Continuously Review and Adapt: The threat landscape evolves; so should your plans.
- Foster Security Awareness: Engage employees across all levels to act as the first line of defense.
- Leverage Third-Party Expertise: External assessments provide valuable impartial feedback.
Real-World Lessons: Resilience in Action
- Maersk (2017 NotPetya Attack): A single surviving domain controller saved the shipping giant from total collapse, proving the value of offsite backups and rigorous DR.
- Target (2013 Data Breach): Poor vendor management and delayed response led to massive financial and reputational losses, spurring IR improvements across industries.
- AWS (2021 Outage): Even cloud leaders face disruptions. Clients with robust DR plans minimized impacts, highlighting the need for shared responsibility models.
Conclusion: Resilience Is an Ongoing Commitment
Absolute security and 100% uptime are unattainable. The most resilient organizations accept this reality and focus on building agile, layered defenses coupled with the ability to respond and recover effectively.
Developing, testing, and refining integrated Incident Response and Disaster Recovery plans is not a one-time project but a continuous cycle of preparation, practice, and improvement. In today’s volatile threat landscape, the difference between catastrophic loss and manageable disruption often lies in the strength of your IR and DR frameworks.
The time to build that strength is before — not during — the next crisis.
